After writing the AWS VPN via VPC to Fortigate firewall blog post, a friend asked if I could do the same for setting up a site-to-site VPN with CenturyLink Cloud.
I agreed!
One warning – you can only VPN between RFC1918 (or private) addressing. If you have a mixed network like I have in my lab then the VPN can only exchange traffic between these private addresses.
Let’s start with the Fortigate! The configuration and screenshots are from FortiOS 5.4 on a Fortigate 200D and I’m using port13 as my uplink port.
Just like we started with creating a VPN to AWS (see post) we need to create the phase1 and phase2 interfaces and the tunnel interface:
config vpn ipsec phase1-interface
edit "to-CTL"
set interface "port13"
set keylife 28800
set proposal aes256-sha256
set dhgrp 5
set nattraversal disable
set remote-gw 64.94.XX.XX
set psksecret S3kR3tZ
next
end
config vpn ipsec phase2-interface
edit "to-CTL"
set phase1name "to-CTL"
set proposal aes192-sha1
set dhgrp 5
set src-addr-type ip
set keylifeseconds 3600
set src-start-ip 64.244.XX.XX
set dst-subnet 10.144.184.0 255.255.255.0
next
end
config system interface
edit "to-CTL"
set vdom "root"
set type tunnel
set interface "port13" # probably WAN1
next
end
If you want to then run some diagnostics, you’d see an error like the following:
ike 0: comes 64.94.XX.XX:500->64.244.XX.XX:500,ifindex=22.... ike 0: IKEv1 exchange=Identity Protection id=b83bc5788a2fb9e3/0000000000000000 len=148 ike 0: in B83BC5788A2FB9E300000000000000000110020000000000000000940D00004400000001000000010000003801010801B83BC5788A2FB9E3000000280001000080010007800E01008004000580020004800B0001000C000400007080800300010D000014AFCAD71368A1F1C96B8696FC7757010000000020699369228741C6D4CA094C93E242C9DE19E7B7C60000000500000500 ike 0:b83bc5788a2fb9e3/0000000000000000:0: responder: main mode get 1st message... ike 0:b83bc5788a2fb9e3/0000000000000000:0: VID DPD AFCAD71368A1F1C96B8696FC77570100 ike 0:b83bc5788a2fb9e3/0000000000000000:0: VID unknown (28): 699369228741C6D4CA094C93E242C9DE19E7B7C60000000500000500 ike 0:to-CTL: ignoring IKE request, no policy configured ike 0:b83bc5788a2fb9e3/0000000000000000:0: negotiation failure ike Negotiate ISAKMP SA Error: ike 0:b83bc5788a2fb9e3/0000000000000000:0: no SA proposal chosen
And all that is doing is telling us that the CenturyLink side is trying to start an IPSEC connection with our Fortigate but as there isn’t a policy created to allow the connection set up to finish.
Adding the policies is straight forward via the GUI or via the CLI (below is a command line example):
config firewall policy
edit 192
set srcintf "to-CTL"
set dstintf "VLAN_0041"
set srcaddr "ctl-10.144.184.0/24"
set dstaddr "internal 192.168.247.0/24"
set action accept
set schedule "always"
set service "ALL"
set logtraffic all
next
edit 193
set srcintf "VLAN_0041"
set dstintf "to-CTL"
set srcaddr "internal 192.168.247.0/24"
set dstaddr "ctl-10.144.184.0/24"
set action accept
set schedule "always"
set service "ALL"
set logtraffic all
next
end
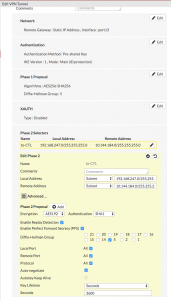
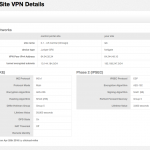
If you look at the GUI configuration for the VPN tunnel it will look something like this:
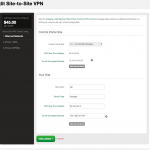
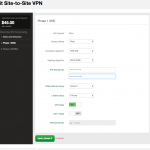
The CenturyLink side configuration from within their web-based GUI console:
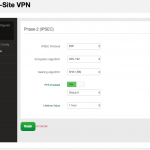
and the result:
..the ping results:
mx:~ % ping -c 5 10.144.184.171 PING 10.144.184.171 (10.144.184.171): 56 data bytes 64 bytes from 10.144.184.171: icmp_seq=0 ttl=52 time=14.663 ms 64 bytes from 10.144.184.171: icmp_seq=1 ttl=52 time=14.769 ms 64 bytes from 10.144.184.171: icmp_seq=2 ttl=52 time=14.705 ms 64 bytes from 10.144.184.171: icmp_seq=3 ttl=52 time=14.695 ms 64 bytes from 10.144.184.171: icmp_seq=4 ttl=52 time=14.621 ms --- 10.144.184.171 ping statistics --- 5 packets transmitted, 5 packets received, 0.0% packet loss round-trip min/avg/max/stddev = 14.621/14.691/14.769/0.049 ms
Need a book to get you started?